Sponsored by F5
Sponsored by F5
Attacker Economics - What Makes Your Company a Prime Target?
Sponsored by F5
Adopting Cross-Function, Cost-Out and Revenue-In Capabilities
Sponsored by Remediant
EMA Evaluation Guide to Privileged Access Management (PAM)
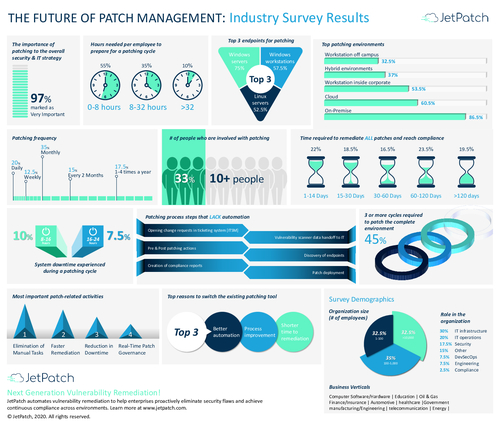
Sponsored by JetPatch
Infographic: The Future of Patch Management
Sponsored by ISC2
10 Reasons Why Businesses Need to Invest in Cloud Security Training
Sponsored by BSI Group
Payment Card Industry Data Security Standard (PCI DSS)
Sponsored by BSI Group
IoT and Operational Technology: Who Should Close the Security Gap?
Sponsored by BSI Group
Determining the Effectiveness of an Incident Response Plan
Sponsored by BSI Group
Effective Vulnerability and Remediation Management
Sponsored by BSI Group
Now is Not the Time for Complacency on Cybersecurity in Healthcare
Sponsored by Tenable
Tenable's 2020 Threat Landscape Retrospective
Sponsored by Tenable
SANS Buyer Guide
Sponsored by Shape Security
Excellence in Digital Experience: The Intersection of Process & Technical Exponentiality
Sponsored by ISC2